Why a NIST based solution?
Cybersecurity best practices require a NIST based solution that follows OCR audit protocol. NIST and their Cyber Security Framework (CSF) is what we follow in the Streamlinz Risk Analysis.
What is the NIST CSF
Many groups claim best practices for cybersecurity, but they are long and difficult to understand. The CSF breaks down the cyber risks and makes its management easier, to allow for immediate remediation. It simplifies the language of cybersecurity so that everyone can understand and move quickly toward compliance.
The core functions of the NIST CSF include:
Identify
The Identify function helps you to develop an overall risk management approach to cybersecurity. It helps you understand your critical assets, business environment, governance model, and vendors/suppliers in your environment.
Protect
Protect helps you determine what controls need to be in place based on your critical assets, risk tolerance, and other input that has been identified. Key aspects of this function are securing access, protecting data, and ongoing education of stakeholders.
Detect
Attacks can come at any time and may not be initially apparent. By having the proper policies in place, this function shortens the time to discovery by spotting anomalies, investigating events, and continuous monitoring.
Respond
Responding quickly via incident response planning, analysis, mitigation, and communication is key to minimizing disruption and costs.
Recover
After an incident, the recover function helps you restore operations through recovery planning, continuous improvement, and communications.
Let's get started protecting your assets
Core Protection
Core Plan Offering Includes:
Privacy Review
Security Review
Automated Task Reminders
Remediation History
Yearly Assessments
Custom Reporting
Industry Updates
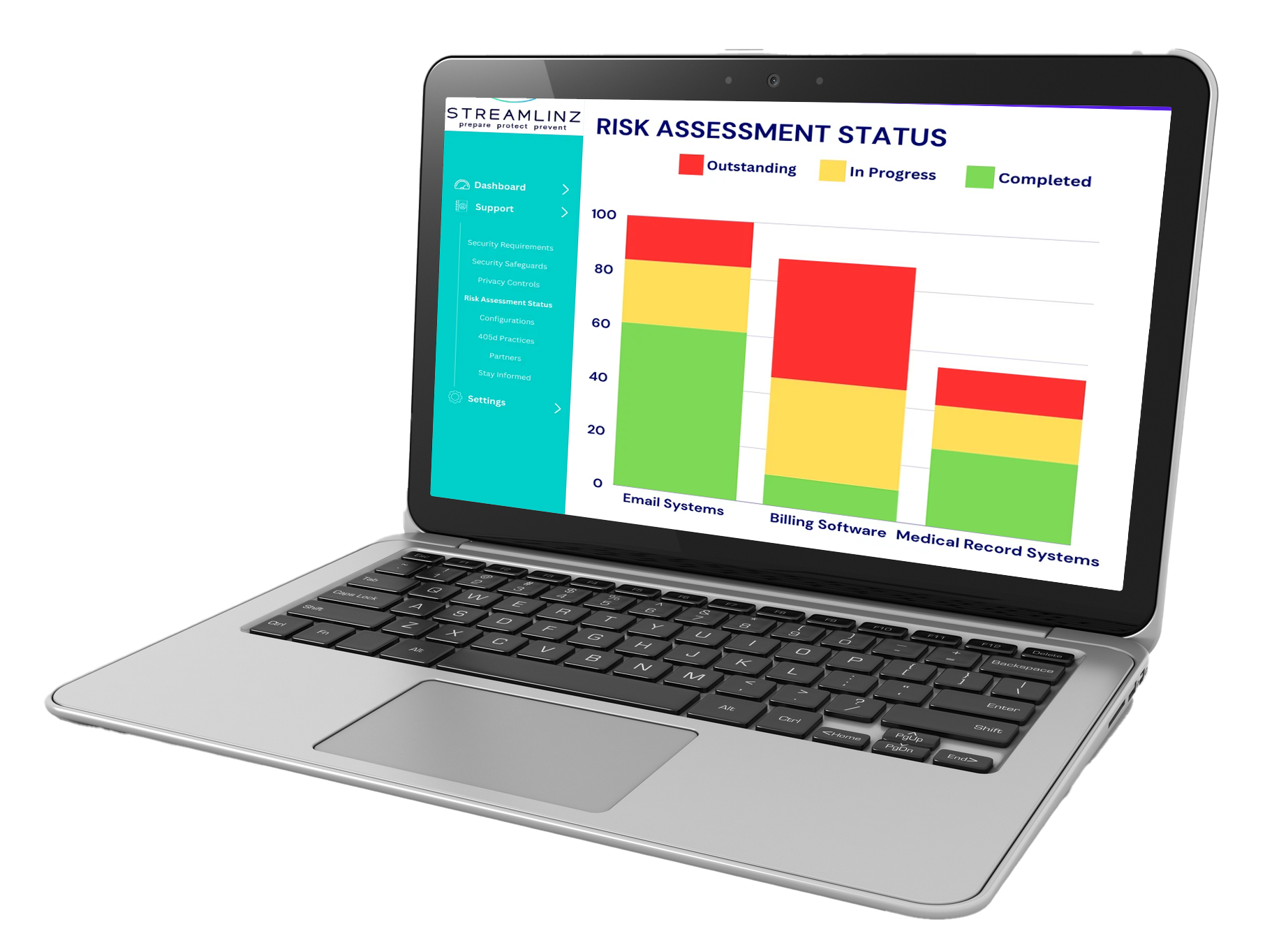
Risk Assessment
405 (d) HICP Review
Predictive Risk Calculations
Policy and Procedure Library
Education Sessions
Full Protection
Full Plan Offering Includes:
Privacy Review
Security Review
Automated Task Reminders
Remediation History
Yearly Assessments
Custom Reporting
Industry Updates
Risk Assessment
Predictive Risk Calculations
405 (d) HICP Review
Policy and Procedure Library
Education Sessions
Exceptional Protection
Exceptional Plan Offering Includes:
Privacy Review
Security Review
Automated Task Reminders
Remediation History
Yearly Assessments
Custom Reporting
Industry Updates
Risk Assessment
Predictive Risk Calculations
405 (d) HICP Review
Policy and Procedure Library
Education Sessions
Cost of Non-Compliance
Streamlinz At a Glance
%
Small businesses report closing their doors 6 months after a large data breach
Average fine PER Breach, for small companies
Streamlinz templates available
Years in the Industry
Hear Why So Many Organizations Love Using Streamlinz
Dr. Darryl K.
The team came onsite and audited our polices and procedures and put a plan in place that now is effective and automated.
Cara R.
Billing Manager, AMS
The automation and review tools within the product were intuitive and complete, allowing us to pinpoint the areas that required immediate remediation.
Dr. Tina S
Family Practitioner
The service team is friendly and knowledgeable, addressing our needs effectively with one call.
Streamlinz cuts HIPAA compliance risks and keeps you protected. Prepare, Protect and Prevent - Our solutions save you time with a guaranteed positive ROI.
Get personalized care and expert guidance to achieve your compliance goals.

949-994-9689
Have Questions? Ask Us Anything!
Read the latest tips and news in the compliance world.

AI in the Healthcare Space: Is Your Usage HIPAA Compliant?
It is the one topic you cannot seem to escape no matter what setting you are in. Whether you’re...

Holiday Hold Ups: Issues with Compliance During the Holiday Season
Picture this: You are sitting by the fire, under a warm blanket, while watching the twinkling...

2025 HIPAA Security Rule Updates: What Your Practice Needs to Know
https://vimeo.com/1130797421?fl=pl&fe=sh
